Two key points to consider when implementing secure remote access to assets on the shopfloor
In this part of our blog series, we address two key points that should be considered for the successful implementation of remote access projects. Firstly, we discuss the preparation stage, during which the industrial assets on the shopfloor are reviewed and those that need to be connected for the project are selected. Secondly, we review issues that might arise when using remote access in an industrial environment.
1. Which industrial assets should be connected and why?
Digitalization allows manufacturers to collect machine and process data that provides the basis for optimizing production, providing predictive maintenance and increasing efficiency.
The first and most important step will be to decide what the purpose of establishing industrial connectivity is:
- Which results are expected from the digitalization project?
- Is data being collected to improve performance in an assembly line, or do we need it to monitor tool wear or potential quality issues?
- Do we want to observe just one machine, one assembly line or the shopfloor/plant as a whole?
- Or do we plan to connect not just one plant, but multiple plants in different locations/countries to get a complete overview of the company’s production?
Depending on the answer to these questions, step two will be to take stock of all assets on the shop floor and consider what information can be gained from them and how that could benefit the company. There may, for example, be machines in the plant that were installed 20 years ago. If they are still an integral part of the production process, then consideration of how legacy software can safely be connected will be an issue. If they are only used for supplementary tasks or back-up and/or likely to be replaced in the near future, it will not make sense to add them to a monitoring system.
The third step is the selection of the right tools to establish connectivity between the chosen industrial assets and the monitoring system. For this step, it is important to understand which protocols and types of connection are used by the assets to establish connectivity. If devices from different vendors are used, it is especially important to consider how all of these can be connected via a vendor-independent solution. TTTech Industrial’s edge computing platform Nerve is an example of such a solution. Installed on the industrial assets at the shopfloor, it provides features to collect data via different types of connections, but also to install, manage and update software applications or controllers from different vendors on the machine.
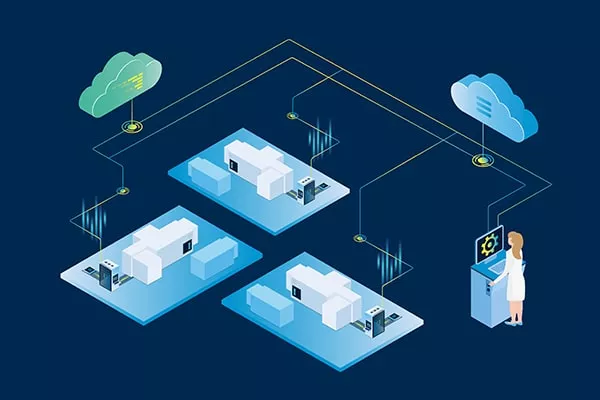
Nerve is an industrial edge computing solution that connects industrial assets and allows users to visualize data and manage software and applications via a central Management System (© TTTech Industrial)
2. What are possible issues when using remote access?
As mentioned before, cybersecurity can be a big issue for industrial connectivity. In an IT context, the “human endpoint” is the weakest link when it comes to cybersecurity. In an OT (operational technology) environment, complexity is added through the industrial assets themselves. They often contain confidential data related to the machines’ performance and the company’s production processes and they are usually more difficult to secure than e.g. a laptop or server in an IT environment.
Not only are there many different types of industrial assets – all of these assets require different types of connectivity solutions. When looking at a multi-core edge server, for example, this might host a number of virtual machines (VMs), as well as a software-defined networking (SDN) management entity or a baseboard management controller (BMC). Each of these may in turn have one or more management or data interfaces that the manufacturer is considering for remote access for their application. Depending on the asset, remote access can be established via command-line shell interfaces, a webservices-based REST API, OPC UA servers, or graphical user interfaces (GUI) via HTML5 – and of course the remote users might prefer desktop access via e.g. VNC (virtual network computing), TeamViewer, RDP (remote desktop protocol) or Xserver.
Another important issue is that not all interfaces for connecting industrial assets are using the latest authentication and connections methods, as they were commonly used only within a trusted, company-internal network (or not connected at all). Some assets, for example, allow access to data via unencrypted HTTP protocols. In such a case, it is important to ensure that the connection can only be established via trusted counterpoints or tunneling over a secure transport protocol. The more people require access to an industrial asset and the wider the range of the network is (be it across several plants, or across countries), the more important security considerations become. No network can be guaranteed to be 100% secure, therefore it is important to implement security measures to ensure that each asset connected to a network has a minimum security level (security level 2 according to IEC 62443).
In our next blog post, we will take a closer look at ways of establishing secure remote access.
This blog post is based on a technical article that was written for and first published in Industrial Ethernet Book (July/August edition 2021). You can find the full article here at iebmedia.com.